Proofpoint's cybersecurity experts were able to identify a large-scale malware campaign that was also imitated by the Federal Central Tax Office. The malware used, which the attackers themselves called “Voldemort”, was distributed via phishing emails.
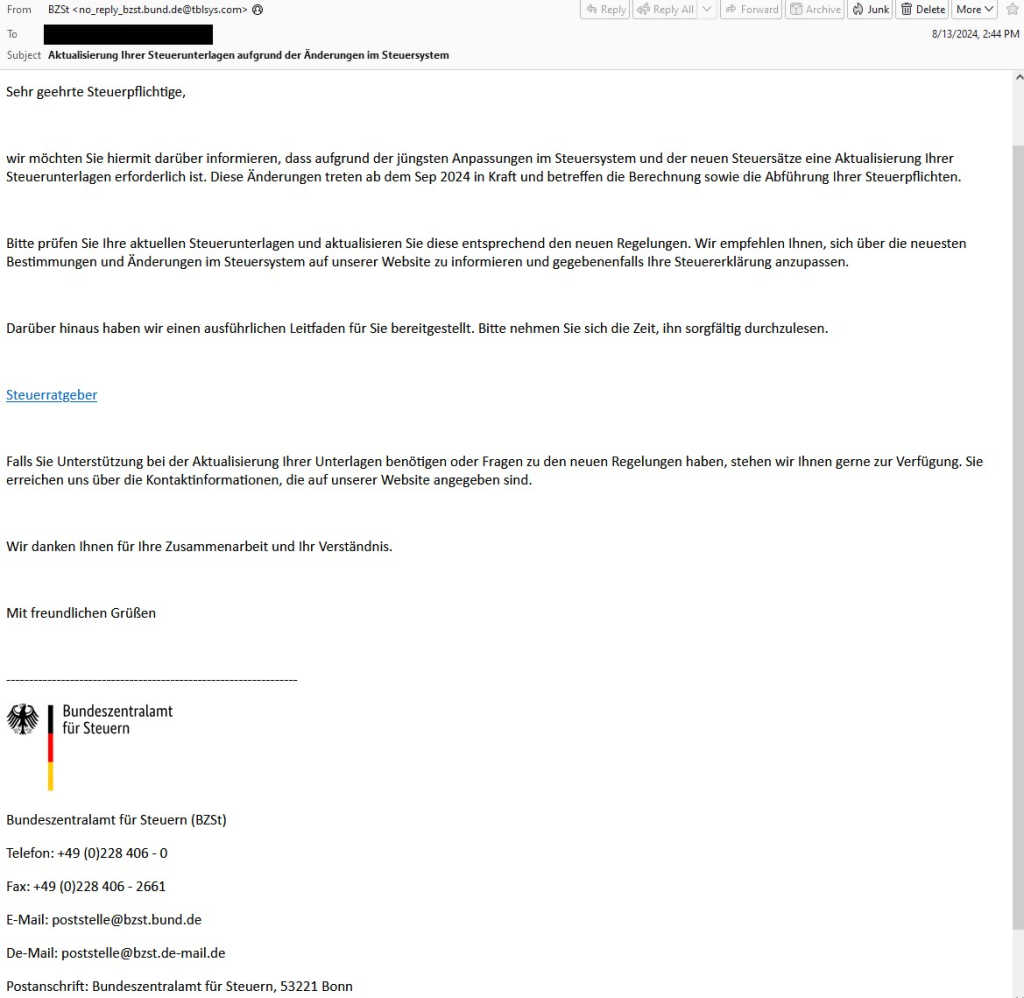
To ensure that as many recipients as possible fall for these messages, the attackers posed as tax authorities from various countries – including the Federal Central Tax Office (see screenshot).
Proofpoint believes that the perpetrators' activities were intended for espionage purposes because the malware includes information gathering functions and the ability to download additional malicious programs. As part of the campaign, over 20,000 emails were sent to over 70 organizations worldwide. What is striking is the combination of common and unusual techniques, including the use of Google Sheets to control the malware (C2) and the exploitation of a vulnerability related to saved search files (.search-ms). Analysis of the malware, written in C, revealed that it collects information about infected computers and sends it to the attackers.
What is particularly striking is the complex attack chain, which includes several steps: First, the victims are lured to fake websites that perform a user agent check. Then, a Windows search is manipulated via a .search-ms file in order to execute the malicious code. This consists of a Python script that collects further information about the system and finally downloads and executes the actual malware, disguised as legitimate files.
Proofpoint also found that the attackers used the Google Sheets infrastructure not only for command and control, but also for exfiltrating data and executing commands on the infected machines. By analyzing Google Sheets, the security analysts were able to gather information about the victims and the commands they executed. They also found evidence of the OpenWRT firmware and a compromised Cobalt Strike server, which may be linked to other activities of the attackers.
Although there are many signs of espionage, the campaign also had characteristics more commonly associated with cybercrime, such as high email volume and the use of techniques commonly used by cybercriminals. Proofpoint was unable to link the campaign to any known hacker group. The combination of sophisticated and simple techniques makes it difficult to assess the attackers' capabilities and their ultimate goals.
The Voldemort campaign is an example of the increasing complexity and sophistication of cyber attacks. The blurring of the lines between espionage and cybercrime and the combination of known and new techniques highlight the challenges facing companies and security researchers today.
(Pounds/Proofpoint)